Have you ever thought of how your cloud flows keep working even after you diligently followed your company policy and updated your password a few times in a row?
I am not necessarily going to be 100% accurate below. Would be happy to be 80% close, and, please, feel free to drop me a note if this requires corrections.
First of all, there is this article which describes the overall architecture:
https://learn.microsoft.com/en-us/power-platform/admin/security/connect-data-sources
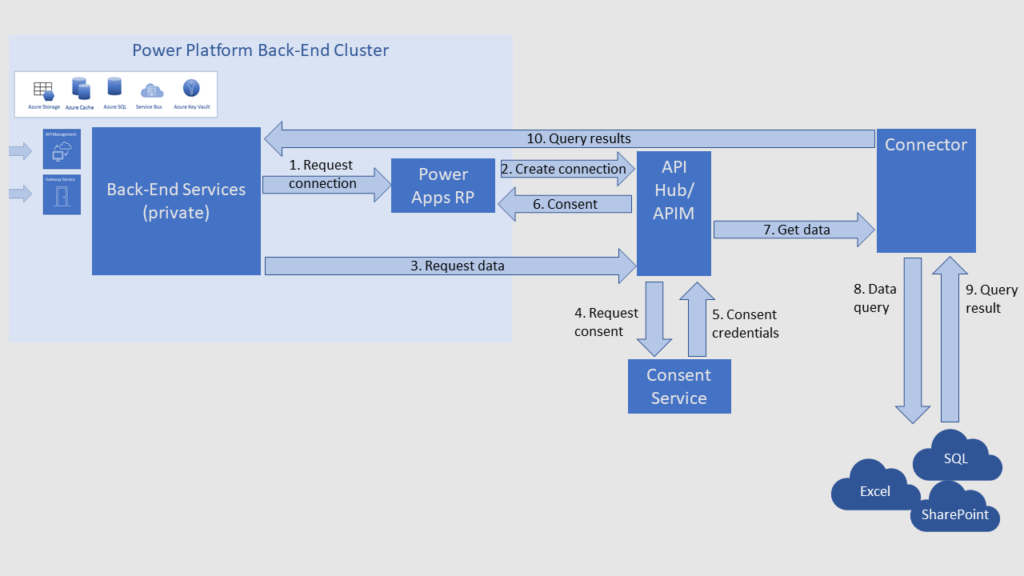
Aside from being quite educational overall, it mentions something very specific:
The API Hub credentials service always stores and manages credentials.
So we know which component stores and manages all those credentials… even if it’s not clearly depicted above, but, apparently, it would be somewhere in that API Hub / APIM area.
Now back to Power Automate connectors for a second. A lot of them would be using Azure AD OAuth:
https://learn.microsoft.com/en-us/connectors/custom-connectors/azure-active-directory-authentication
With that, we should be talking about access tokens and refresh tokens:
https://learn.microsoft.com/en-us/azure/active-directory/develop/refresh-tokens
Access tokens are required to access resources. However, they expire quickly. Refresh tokens are used to refresh access tokens without having to re-enter credentials, and they have a lifespan of up to 90 days as per the link above.
I believe we should be looking at the rightmost column in the table there:
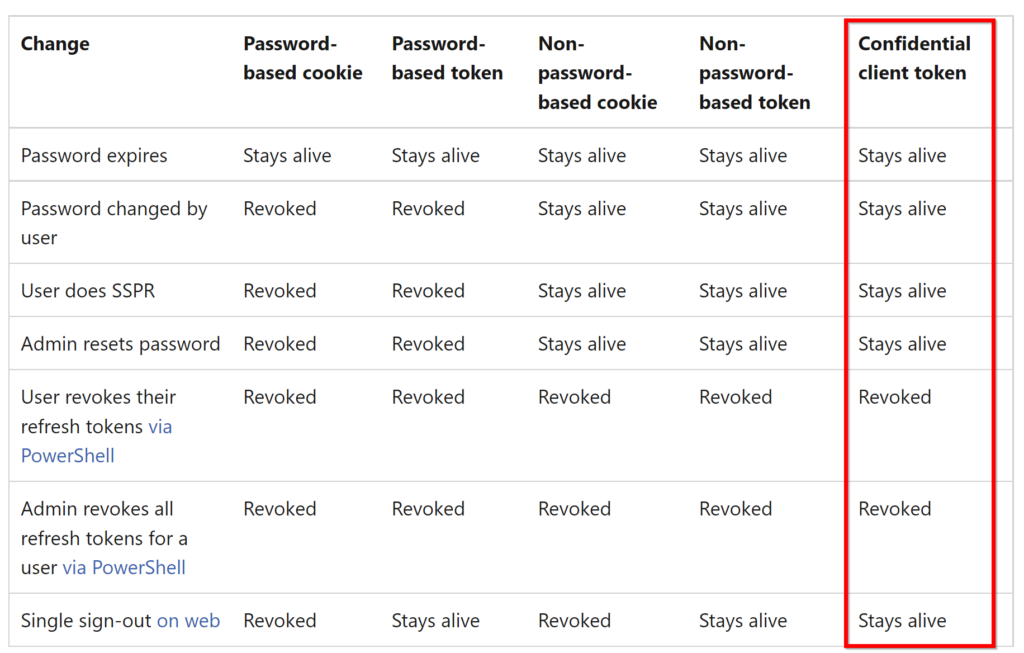
A confidential client application is an application that can be trusted to hold a secret and present that secret when requesting access tokens. Examples of confidential applications are server-side applications:
So, to summarize:
- Let’s say there is a connector that has an associated app registration in Azure
- That app represents a confidential client
- Since it’s a confidential client, once a refresh token has been issued to it, it can keep using that refresh token “forever” on until it’s been explicitly revoked
- That refresh process, from the Power Automate perspective, is performed by the API Hub credentials service component of the Power Platform back-end cluster
Hm… seems to make sense?