Before you read this post, let me suggest two earlier posts first, since they are all part of the same series:
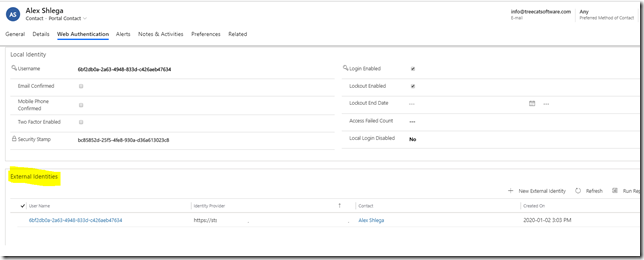
Power App Portals have identity management functionality available out of the box. What it means is that the portals can use local identities, but they can also use external identities (azure, google, facebook, etc). All those identities can be linked to the same user profile in the portal (contact record in CDS):
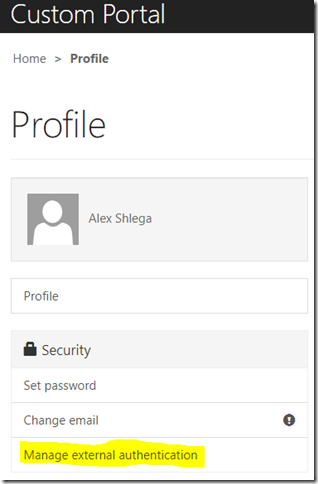
Once a portal user has logged in using some kind of authentication, they can manage their other external authentications from the profile page:
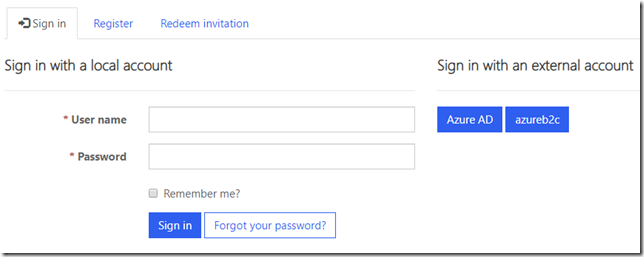
For example. I just set up Azure AD B2C integration for my portal (have a look at the previous post for more details). However, I did not limit portal sign in options to the azureb2c policy only (through the LoginButtonAuthenticationType parameter), so “local account” and “Azure AD” are still there:
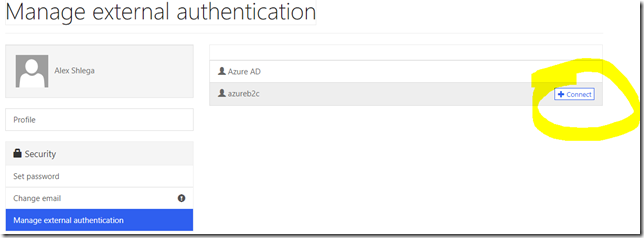
If I sign in through Azure AD, I’ll be able to connect my other external identities to my portal profile – in this case I only have azureb2c configured, so there are not a lot of options, but I could have configured google and facebook, for example, in which case they would be showing up on the list as well:
This is where the difference between using Azure AD B2C as an external identity provider and utilizing those other “individual” identity providers becomes clearer.
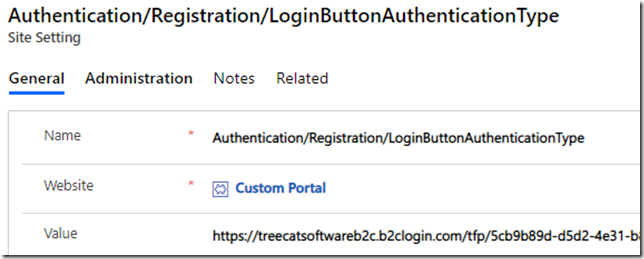
When Azure AD B2C is available, it’s likely the only identity provider the portal needs to know about, so it only makes sense to instruct the portal to use that identity provider all the time through the following site setting:
Authentication/Registration/LoginButtonAuthenticationType
When done that way, “sign in” link on the portal will bring the users directly to the Azure AD B2C sign in page:
So… there is no Azure AD or other options there? This is because I now need to go back to the Azure AD B2C and configure required identity providers as described in the docs:
https://docs.microsoft.com/en-us/azure/active-directory-b2c/tutorial-add-identity-providers
Note: it seems Azure AD application setup instructions provided there might not work as is, at least they did not work for me. When specifying the redirect url for my Azure AD application, I had to use the following format:
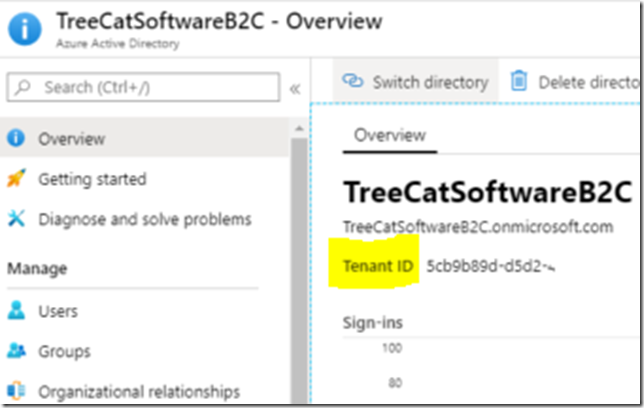
https://treecatsoftwareb2c.b2clogin.com/5cb9b89d-d5d2-4e31-….-e82a2cf12121/oauth2/authresp
That ID in the url is my Azure AD B2C tenant ID:
Otherwise, I kept getting an error when trying to authenticate through Azure AD since the redirect url specified for my application was different from the redirect url added to the request by Azure AD B2C when it was “redirecting” authentication to Azure AD (Uh… would be good if you are still following me, since I seem to be loosing it myself in all those redirects).
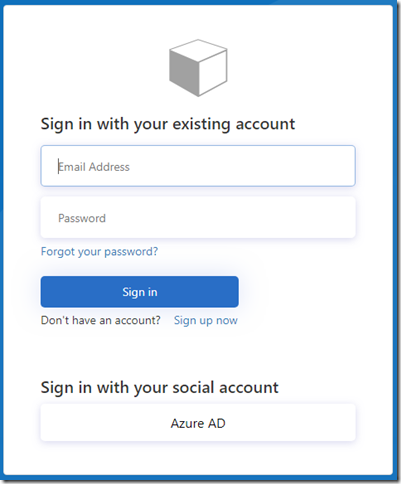
Anyway, once I’ve done that, Azure AD is now showing up as a “social account” sign in option on the Azure AD B2C sign in page:
If I use it to sign in, that brings me to the other screen:
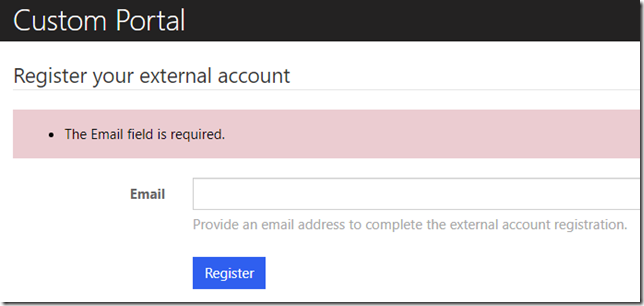
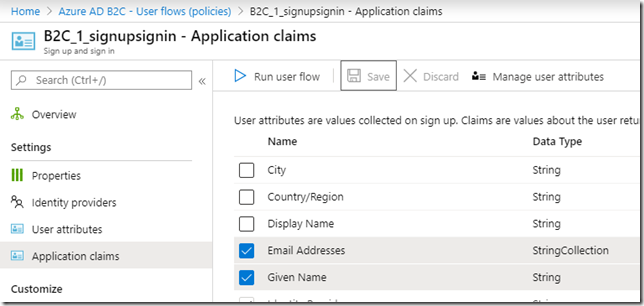
Another note: I did not enable email claim on my B2C signin flow, so, at first, once I passed through the screen above, I got the following page displayed on the portal:
This is not how it should be, so, if you happen to forget to enable that claim as well, just go to you Azure AD B2C portal, find the signin policy you have set up for the portal, and add email claim there:
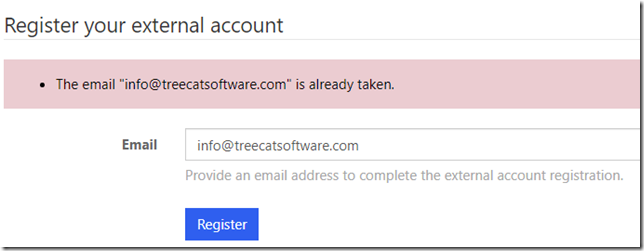
Once I’ve done that, though, the portal is complaining again:
But this is normal. The portal is not allowing a registration for an email that’s already there – remember that original portal account was using Azure ID external identity; however, right now I’m trying to register with an Azure AD B2C external identity, and it’s different. So, the portal is trying to create a new contact record in CDS with the same email address, and it can’t.
There is a portal setting that allows auto-association to a contact record based on email:
https://docs.microsoft.com/en-us/powerapps/maker/portals/configure/azure-ad-b2c#claims-mapping
If I wanted to enable that setting, I would need to add the following site setting to the portal my Azure AD B2C external provider (and set the value to true):
Authentication/OpenIdConnect/azureb2c/AllowContactMappingWithEmail
Finally, once that is done, I can now login to the portal through Azure AD B2C… but still using my Azure AD identity.
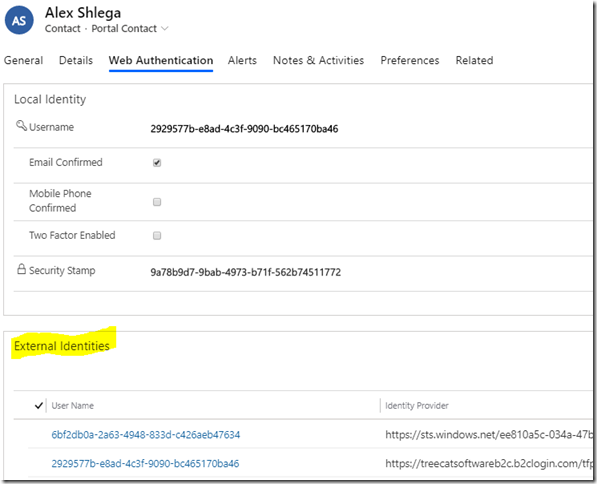
Since I did set up the portal (see above) to use Azure AD B2C exclusively, I don’t see my other external identities (or the local portal identity) on the profile page:
However, behind the scene the portal just created another external identity for my contact record:
It’s almost all good so far except for one remaining question (I know there are more questions, but this one is important). Having the portal integrated with Azure AD B2C, I would think there should be some easy way to link multiple external identities to the same user account. Basically, what if a portal user had different external identities(Azure AD, Google, Facebook, etc) and wanted to use either of them to login into the same portal account?
While identity management was done by the portal, it was possible to connect external identities from the user profile screen.
However, since I have just outsourced identity management to the Azure AD B2C, that kind of linkage would have to be done through Azure AD B2C now.
This seems to be what the github repository below is meant for, but I am certainly going to have to spend some more time on it:
https://github.com/Azure-Samples/active-directory-b2c-advanced-policies/tree/master/account-linking
And this will have to wait until the next post.
Great articles Alex thanks for sharing !
I have manged to set up Azure AD B2C authentication but we have a requirement to only allow existing CRM contacts to sign up.
I know this is possible through the invitation code but this only applies to local authentication (as in authentication is managed internally within CRM) and not Azure AD B2C.
So it looks like we have to go down the path of custom policies.
https://docs.microsoft.com/en-us/azure/active-directory-b2c/custom-policy-get-started?tabs=applications
This allows customising of the login page so that we can do some validation of the user’s email against CRM before they get to sign up via Jscript.
Seems like it is very complicated so I’m wondering if you or know anyone who has successfully implemented custom policies? I might be totally wrong here in suggestion custom policies but it doesn’t look like there is any other way to restrict user sign up.