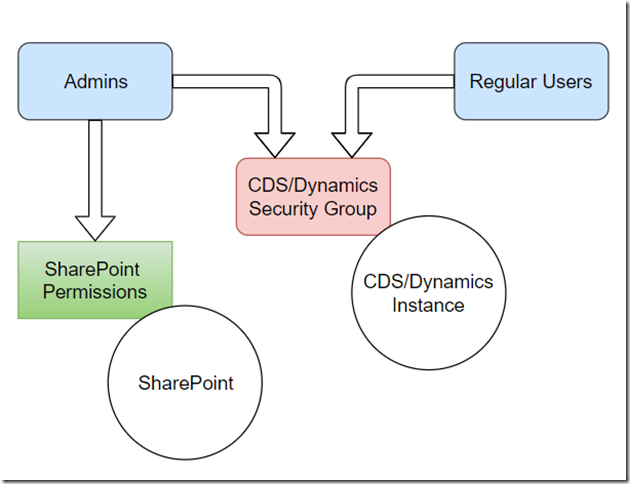
This post is a proof of concept for the following scenario:
Would not it be nice if we could use more than one security group so that, for example, we would have admins in one group and all the other users in another. This way, we might add that admin group to Sharepoint so admin users would become site owners/site collection admins there.
Unfortunately, nested security groups are not supported for CDS/Dynamics:
Do we have any options? Well, just continuing on the PowerShell exploration path that I started earlier this month, we could use this kind of script to emulate nested groups:
install-module azuread
import-module azuread
Connect-AzureAD
$GroupStartWith = 'Root_CRM'
$ADGroups = get-azureadgroup -Filter "startswith(DisplayName, '$GroupStartWith')"
foreach ($ADGroup in $ADGroups) {
$Members = Get-AzureADGroupMember -ObjectId $ADGroup.ObjectId
#Delete all "user-members"
foreach ($Member in $Members)
{
if($Member.ObjectType -eq "User")
{
Remove-AzureADGroupMember -ObjectId $ADGroup.ObjectId -MemberId $Member.ObjectId
}
}
#Re-add all nested user-members
foreach ($Member in $Members)
{
if($Member.ObjectType -eq "Group")
{
$NestedMembers = Get-AzureADGroupMember -ObjectId $Member.ObjectId
foreach ($NestedMember in $NestedMembers)
{
if($NestedMember.ObjectType -eq "User")
{
#Write-Host $NestedMember
Add-AzureADGroupMember -ObjectId $ADGroup.ObjectId -RefObjectId $NestedMember.ObjectId
}
}
}
}
}
What the script above would do is:
– It would connect to Azure AD
– It would find all groups named as “Root_CRM*” – that’s just a quick “naming convention” I came up with just now
– The script will, then, loop over all of those groups and do a couple of things for each of those:
- It will remove all current members
- It will look at the nested groups and add nested group members to the main group
As a result, I can have security groups configured exactly the way it’s shown on the diagram above since I’m not limited to having just one group anymore.
Of course it’s PowerShell, so the script has to be started somehow. It might be doable with Azure Runbooks – for example, this script could be scheduled to run a few times per day to do the automated sync. Although, it will have to be updated so it does not ask for the credentials. Which should be doable with Get-AutomationConnection
Yet the script can likely be improved so it does not remove users which will be re-added eventually. This is to avoid possible glitches when a user loses access to CDS/Dynamics for a moment while that user is being re-added.